Questo tutorial è Copyright (c) 2012 di Falko Timme. È derivato da un tutorial di Christoph Haas che puoi trovare su http://workaround.org. Sei libero di utilizzare questo tutorial con la licenza Creative Commons 2.5 o qualsiasi versione successiva.
Questo documento descrive come installare un server di posta Postfix basato su utenti e domini virtuali, ovvero utenti e domini che si trovano in un database MySQL. Dimostrerò anche l'installazione e la configurazione di Courier (Courier-POP3, Courier-IMAP), in modo che Courier possa autenticarsi sullo stesso database MySQL utilizzato da Postfix.
Il server Postfix risultante è in grado di SMTP-AUTH e TLS e quota (quota non è incorporata in Postfix per impostazione predefinita, mostrerò come applicare una patch a Postfix in modo appropriato). Le password sono archiviate in crittografate modulo nel database (la maggior parte dei documenti che ho trovato riguardavano password in testo normale, il che rappresenta un rischio per la sicurezza). In aggiunta a ciò, questo tutorial copre l'installazione di Amavisd , SpamAssassin e ClamAV in modo che le e-mail vengano scansionate alla ricerca di spam e virus. Mostrerò anche come installare SquirrelMail come interfaccia webmail in modo che gli utenti possano leggere e inviare e-mail e modificare le proprie password.
Il vantaggio di tale configurazione "virtuale" (utenti virtuali e domini in un database MySQL) è che è molto più performante di una configurazione basata su utenti di sistema "reali". Con questa configurazione virtuale il tuo server di posta può gestire migliaia di domini e utenti. Inoltre, è più facile da amministrare perché hai a che fare con il database MySQL solo quando aggiungi nuovi utenti/domini o modifichi quelli esistenti. Niente più comandi postmap per creare file db, niente più ricarica di Postfix, ecc. Per l'amministrazione del database MySQL puoi usare strumenti web based come phpMyAdmin che sarà installato anche in questo howto. Il terzo vantaggio è che gli utenti hanno un indirizzo e-mail come nome utente (invece di un nome utente + un indirizzo e-mail) che è più facile da capire e tenere a mente.
Questo howto vuole essere una guida pratica; non copre le basi teoriche. Sono trattati in molti altri documenti nel Web.
Questo documento viene fornito senza garanzie di alcun tipo! Voglio dire che questo non è l'unico modo per creare un sistema del genere. Ci sono molti modi per raggiungere questo obiettivo, ma questo è il modo in cui prendo. Non garantisco che questo funzionerà per te!
1 Nota preliminare
Questo tutorial è basato su Ubuntu 12.10 Server (Quantal Quetzal), quindi dovresti configurare un'installazione di base del server Ubuntu 12.10 prima di continuare con questo tutorial. Il sistema dovrebbe avere un indirizzo IP statico. Uso 192.168.0.100 come indirizzo IP in questo tutorial e server1.example.com come nome host.
Assicurati di aver effettuato l'accesso come root (digita
sudo su
per diventare root), perché dobbiamo eseguire tutti i passaggi di questo tutorial come utente root.
È molto importante rendere /bin/sh un collegamento simbolico a /bin/bash...
dpkg-reconfigure dash
Utilizzare dash come shell di sistema predefinita (/bin/sh)? <-- No
... e che disabiliti AppArmor:
/etc/init.d/apparmor stop
update-rc.d -f apparmor remove
apt-get remove apparmor apparmor-utils
2 Installa Postfix, Courier, Saslauthd, MySQL, phpMyAdmin
Per installare Postfix, Courier, Saslauthd, MySQL e phpMyAdmin, eseguiamo semplicemente
apt-get install postfix postfix-mysql postfix-doc mysql-client mysql-server courier-authdaemon courier-authlib-mysql courier-pop courier-pop-ssl courier-imap courier-imap-ssl libsasl2-2 libsasl2-modules libsasl2-modules-sql sasl2-bin libpam-mysql openssl phpmyadmin apache2 libapache2-mod-php5 php5 php5-mysql libpam-smbpass
Ti verranno poste alcune domande:
Nuova password per l'utente "root" di MySQL:<-- yourrootsqlpassword
Ripetere la password per l'utente "root" di MySQL:<-- yourrootsqlpassword
Creare directory per l'amministrazione basata sul Web? <-- No
Tipo generale di configurazione della posta:<-- Sito Internet
Nome e-mail del sistema:<-- server1.example.com
Certificato SSL richiesto <-- Ok
Server Web da riconfigurare automaticamente:<-- apache2
Configura il database per phpmyadmin con dbconfig-common? <-- No
3 Applicare la patch di quota a Postfix
Dobbiamo ottenere i sorgenti di Postfix, correggerli con la quota patch, creare nuovi pacchetti Postfix .deb e installare quei pacchetti .deb:
apt-get build-dep postfix
cd /usr/src
apt-get suffisso sorgente
(Assicurati di utilizzare la versione di Postfix corretta nei seguenti comandi. Ho installato Postfix 2.9.3. Puoi scoprire la tua versione di Postfix eseguendo
postconf -d | grep mail_version
L'output dovrebbe essere simile a questo:
[email protetta]:/usr/src# postconf -d | grep mail_version
mail_version =2.9.3
milter_macro_v =$mail_name $mail_version
[email protected]:/usr/src#
)
wget http://vda.sourceforge.net/VDA/postfix-vda-v11-2.9.1.patch
cd postfix-2.9.3
patch -p1 <../postfix-vda-v11 -2.9.1.patch
Quindi apri debian/rules e cambia DEB_BUILD_HARDENING da 1 a 0:
vi debian/rules
[...] export DEB_BUILD_HARDENING=0 [...] |
Se non lo fai, la tua build fallirà con i seguenti messaggi di errore:
maildir.c:nella funzione âdeliver_maildirâ:
maildir.c:974:17:errore:format not a string literal and no format arguments [-Werror=format-security]
maildir.c:977:17 :errore:formattare non una stringa letterale e nessun argomento di formato [-Werror=format-security]
maildir.c:983:17:errore:formattare non una stringa letterale e nessun argomento di formato [-Werror=format-security ]
maildir.c:986:17:errore:format non una stringa letterale e nessun argomento di formato [-Werror=format-security]
maildir.c:Nella funzione âsql2fileâ:
maildir. c:404:25:avviso:ignorando il valore di ritorno di âreadâ, dichiarato con l'attributo warn_unused_result [-Wunused-result]
maildir.c:417:26:avviso:ignorando il valore di ritorno di âwriteâ, dichiarato con l'attributo warn_unused_result [- Wunused-result]
cc1:alcuni avvisi vengono trattati come errori
make:*** [maildir.o] Errore 1
make:Leaving directory `/usr/src/postfix-2.9. 3/src/virtual'
make[1]:*** [aggiornamento] Errore 1
make[1]:Uscita dalla directory `/usr/src/postfix -2.9.3'
make:*** [build] Errore 2
dpkg-buildpackage:errore:debian/rules build ha fornito lo stato di uscita dell'errore 2
[email protected]:/usr/ src/postfix-2.9.3#
Ora possiamo creare i nuovi pacchetti .deb di Postfix:
dpkg-buildpackage
Ora andiamo di una directory in alto, ecco dove sono stati creati i nuovi pacchetti .deb:
cd ..
Il comando
ls -l
ti mostra i pacchetti disponibili:
[email protetta]:/usr/src# ls -l
total 6928
drwxr-xr-x 24 root root 4096 19 ottobre 12:56 linux-headers-3.5.0-17
drwxr-xr-x 7 root root 4096 19 ottobre 12:56 linux-headers-3.5.0-17-generic
drwxr-xr-x 18 root root 4096 nov 4 14:11 postfix-2.9.3
-rw-r--r-- 1 root root 3809 nov 4 14:11 postfix_2.9.3-2ubuntu2_amd64.changes
-rw-r--r-- 1 root 1510254 nov 4 14:11 postfix_2 .9.3-2ubuntu2_amd64.deb
-rw-r--r-- 1 root 249645 nov 4 14:10 postfix_2.9.3-2ubuntu2.diff.gz
-rw-r--r-- 1 root root 1599 4 novembre 14:10 postfix_2.9.3-2ubuntu2.dsc
-rw-r--r-- 1 root 3760555 30 maggio 18:04 postfix_2.9.3.orig.tar.gz
-rw-r--r-- 1 root root 47064 nov 4 14:11 postfix-cdb_2.9.3-2ubuntu2_amd64.deb
-rw-r--r-- 1 root 159634 nov 4 14:11 postfix-dev_2.9.3-2ubuntu2_all.deb
-rw-r--r-- 1 root root 1077006 nov 4 14:11 postfix-doc_2.9.3-2ubuntu2_all.deb
-rw-r-- r-- 1 root root 55430 Nov 4 14:11 postfix-ldap_2.9.3-2u buntu2_amd64.deb
-rw-r--r-- 1 root 48796 nov 4 14:11 postfix-mysql_2.9.3-2ubuntu2_amd64.deb
-rw-r--r-- 1 root 48964 4 novembre 14:11 postfix-pcre_2.9.3-2ubuntu2_amd64.deb
-rw-r--r-- 1 root root 48978 4 novembre 14:11 postfix-pgsql_2.9.3-2ubuntu2_amd64.deb
-rw-r--r-- 1 root root 55009 11 aprile 2012 postfix-vda-v11-2.9.1.patch
[email protetta]:/usr/src#
Scegli i pacchetti postfix e postfix-mysql e installali in questo modo:
dpkg -i postfix_2.9.3-2ubuntu2_amd64.deb postfix-mysql_2.9.3-2ubuntu2_amd64.deb
4 Creare il database MySQL per Postfix/Courier
Ora creiamo un database chiamato mail:
mysqladmin -u root -p create mail
Successivamente, andiamo alla shell MySQL:
mysql -u root -p
Sulla shell MySQL, creiamo l'utente mail_admin con la password mail_admin_password (sostituirla con la propria password) che ha i privilegi SELECT,INSERT,UPDATE,DELETE sul database di posta. Questo utente sarà utilizzato da Postfix e Courier per connettersi al database di posta:
GRANT SELECT, INSERT, UPDATE, DELETE ON mail.* A 'mail_admin'@'localhost' IDENTIFICATO DA 'mail_admin_password';
GRANT SELECT, INSERT, UPDATE, DELETE ON mail.* TO 'mail_admin'@'localhost. localdomain' IDENTIFICATO DA 'mail_admin_password';
PRIVILEGI FLUSH;
Sempre sulla shell MySQL, creiamo le tabelle necessarie a Postfix e Courier:
USE mail;
domini CREATE TABLE (
dominio varchar(50) NOT NULL,
PRIMARY KEY (domain) )
ENGINE=MyISAM;
CREATE TABLE inoltri (
source varchar(80) NOT NULL,
destination TEXT NOT NULL,
PRIMARY KEY (source) )
ENGINE=MyISAM;
CREATE TABLE utenti (
email varchar(80) NOT NULL,
password varchar(20) NOT NULL,
quota INT(10) DEFAULT '10485760',
PRIMARY KEY (email )
) MOTORE=MyISAM;
CREATE TABLE trasporto (
dominio varchar(128) NOT NULL predefinito '',
trasporto varchar(128) NOT NULL predefinito '',
CHIAVE UNICA dominio (dominio)
) MOTORE =MyISAM;
quit;
Come avrai notato, con l'abbandono; comando abbiamo lasciato la shell MySQL e siamo tornati sulla shell Linux.
I domini la tabella memorizzerà ogni dominio virtuale per il quale Postfix dovrebbe ricevere e-mail (ad es. example.com ).
| dominio |
| example.com |
Gli inoltri tabella serve per alias un indirizzo e-mail a un altro, ad es. inoltra email per [email protected] a [email protetta] .
| fonte | destinazione |
| [email protetta] | [email protetta] |
Gli utenti la tabella memorizza tutti gli utenti virtuali (ovvero gli indirizzi e-mail, perché l'indirizzo e-mail e il nome utente sono gli stessi) e le password (in crittografato form!) e un valore di quota per ciascuna casella di posta (in questo esempio il valore predefinito è 10485760 byte che significa 10 MB).
| password | quota | |
| [email protetta] | No9.E4skNvGa. ("segreto" in forma crittografata) | 10485760 |
Il trasporto la tabella è facoltativa, è per utenti avanzati. Permette di inoltrare mail per singoli utenti, interi domini o tutte le mail ad un altro server. Ad esempio,
| dominio | trasporto |
| example.com | smtp:[1.2.3.4] |
inoltrerebbe tutte le email per example.com tramite il protocollo smtp al server con indirizzo IP 1.2.3.4 (le parentesi quadre [] significa "non effettuare una ricerca del record DNS MX" (che ha senso per gli indirizzi IP...). Se invece utilizzi un nome di dominio completo (FQDN), non utilizzeresti le parentesi quadre.).
A proposito, (suppongo che l'indirizzo IP del tuo sistema di server di posta sia 192.168.0.100) puoi accedere a phpMyAdmin su http://192.168.0.100/phpmyadmin/ in un browser e accedere come mail_admin. Quindi puoi dare un'occhiata al database. Successivamente puoi usare phpMyAdmin per amministrare il tuo server di posta.
5 Configura Postfix
Ora dobbiamo dire a Postfix dove può trovare tutte le informazioni nel database. Quindi dobbiamo creare sei file di testo. Noterai che dico a Postfix di connettersi a MySQL sull'indirizzo IP 127.0.0.1 anziché su localhost. Questo perché Postfix è in esecuzione in una prigione chroot e non ha accesso al socket MySQL che proverebbe a connettersi se dicessi a Postfix di usare localhost. Se uso 127.0.0.1, Postfix utilizza la rete TCP per connettersi a MySQL, il che non è un problema nemmeno in una jail chroot (l'alternativa sarebbe spostare il socket MySQL nella jail chroot che causa altri problemi).
Assicurati che /etc/mysql/my.cnf contenga la seguente riga:
vi /etc/mysql/my.cnf
[...] # Instead of skip-networking the default is now to listen only on # localhost which is more compatible and is not less secure. bind-address = 127.0.0.1 [...] |
Se dovessi modificare /etc/mysql/my.cnf, riavvia MySQL ora:
/etc/init.d/mysql restart
Corri
netstat -tap | grep mysql
per assicurarsi che MySQL sia in ascolto su 127.0.0.1 (localhost.localdomain):
[email protetta]:/usr/src# netstat -tap | grep mysql
tcp 0 0 localhost.localdo:mysql *:* ASCOLTA 3895/mysqld
[email protected]:/usr/src#
Ora creiamo i nostri sei file di testo.
vi /etc/postfix/mysql-virtual_domains.cf
user = mail_admin password = mail_admin_password dbname = mail query = SELECT domain AS virtual FROM domains WHERE domain='%s' hosts = 127.0.0.1 |
vi /etc/postfix/mysql-virtual_forwardings.cf
user = mail_admin password = mail_admin_password dbname = mail query = SELECT destination FROM forwardings WHERE source='%s' hosts = 127.0.0.1 |
vi /etc/postfix/mysql-virtual_mailboxes.cf
user = mail_admin password = mail_admin_password dbname = mail query = SELECT CONCAT(SUBSTRING_INDEX(email,'@',-1),'/',SUBSTRING_INDEX(email,'@',1),'/') FROM users WHERE email='%s' hosts = 127.0.0.1 |
vi /etc/postfix/mysql-virtual_email2email.cf
user = mail_admin password = mail_admin_password dbname = mail query = SELECT email FROM users WHERE email='%s' hosts = 127.0.0.1 |
vi /etc/postfix/mysql-virtual_transports.cf
user = mail_admin password = mail_admin_password dbname = mail query = SELECT transport FROM transport WHERE domain='%s' hosts = 127.0.0.1 |
vi /etc/postfix/mysql-virtual_mailbox_limit_maps.cf
user = mail_admin password = mail_admin_password dbname = mail query = SELECT quota FROM users WHERE email='%s' hosts = 127.0.0.1 |
Quindi cambia i permessi e il gruppo di questi file:
chmod o=/etc/postfix/mysql-virtual_*.cf
chgrp postfix /etc/postfix/mysql-virtual_*.cf
Ora creiamo un utente e un gruppo chiamato vmail con la directory home /home/vmail. Qui è dove verranno archiviate tutte le caselle di posta.
groupadd -g 5000 vmail
useradd -g vmail -u 5000 vmail -d /home/vmail -m
Quindi eseguiamo alcune configurazioni di Postfix. Assicurati di sostituire server1.example.com con un FQDN valido, altrimenti Postfix potrebbe non funzionare correttamente!
postconf -e 'myhostname =server1.example.com'
postconf -e 'mydestination =server1.example.com, localhost, localhost.localdomain'
postconf -e 'mynetworks =127.0.0.0/8'
postconf -e 'virtual_alias_domains ='
postconf -e 'virtual_alias_maps =proxy:mysql:/etc/postfix/mysql-virtual_forwardings.cf, mysql:/etc/postfix/mysql-virtual_email2email.cf'
postconf -e 'virtual_mailbox_domains =proxy:mysql:/etc/postfix/mysql-virtual_domains.cf'
postconf -e 'virtual_mailbox_maps =proxy:mysql:/etc/postfix/mysql-virtual_mailboxes.cf'
postconf -e 'virtual_mailbox_base =/home/vmail'
postconf -e 'virtual_uid_maps =static:5000'
postconf -e 'virtual_gid_maps =static:5000'
postconf -e ' smtpd_sasl_auth_enable =yes'
postconf -e 'broken_sasl_auth_clients =yes'
postconf -e 'smtpd_sasl_authenticated_header =yes'
postconf -e 'smtpd_recipient_restrictions =permit_mynetworks, permit_sasl_authenticated, require_unauth_postconfest'
-e 'smtpd_use_tls =yes'
postconf -e 'smtpd_tls_cert_file =/etc/postfix/smtpd.cert'
postconf -e 'smtpd_tls_key_file =/etc/postfix/smtpd.key'
postconf -e 'transport_maps =proxy:mysql:/etc/postfix/mysql-virtual_transports.cf'
postconf -e 'virtual_maildir_extended =yes'
postconf -e 'virtual_mailbox_limit_maps =proxy:mysql:/etc/postfix /mysql-virtual_mailbox_limit_maps.cf'
postconf -e 'virtual_mailbox_limit_override =yes'
postconf -e 'virtual_maildir_limit_message ="L'utente che stai cercando di raggiungere ha superato la quota."'
postconf -e 'virtual_overquota_bounce =yes'
postconf -e 'proxy_read_maps =$ local_recipient_maps $ mydestination $ virtual_alias_maps $ virtual_alias_domains $ virtual_mailbox_maps $ virtual_mailbox_domains $ relay_recipient_maps $ relay_domains $ canonical_maps $ sender_canonical_maps $ recipient_canonical_maps $ relocated_maps $ transport_maps $ mynetworks $ virtual_mailbox_limit_maps'
Successivamente creiamo il certificato SSL necessario per TLS:
cd /etc/postfix
openssl req -new -outform PEM -out smtpd.cert -newkey rsa:2048 -nodes -keyout smtpd.key -keyform PEM -days 365 -x509
Nome del Paese (codice di 2 lettere) [AU]:<-- Inserisci il nome del tuo Paese (ad es. "DE").
Nome Stato o Provincia (nome completo) [Stato-Stato]:<-- Inserisci il tuo Stato o nome della provincia.
Nome località (ad es. città) []:<-- Inserisci la tua città.
Nome organizzazione (ad es. azienda) [Internet Widgits Pty Ltd]:<-- Inserisci il nome dell'organizzazione (ad es. il nome della tua azienda).
Nome dell'unità organizzativa (ad es. sezione) []:<-- Inserisci il nome dell'unità organizzativa (ad es. "Dipartimento IT").
Nome comune (ad es. IL TUO nome) []:<-- Inserisci il nome di dominio completo del sistema (ad es. "server1.example.com").
Indirizzo e-mail []:<-- Inserisci il tuo indirizzo e-mail.
Quindi cambia i permessi di smtpd.key:
chmod o= /etc/postfix/smtpd.key
6 Configura Saslauthd
Prima esecuzione
mkdir -p /var/spool/postfix/var/run/saslauthd
Quindi modifica /etc/default/saslauthd. Imposta START su yes e cambia la riga OPTIONS="-c -m /var/run/saslauthd" in OPTIONS="-c -m /var/spool/postfix/var/run/saslauthd -r":
vi /etc/default/saslauthd
# # Settings for saslauthd daemon # Please read /usr/share/doc/sasl2-bin/README.Debian for details. # # Should saslauthd run automatically on startup? (default: no) START=yes # Description of this saslauthd instance. Recommended. # (suggestion: SASL Authentication Daemon) DESC="SASL Authentication Daemon" # Short name of this saslauthd instance. Strongly recommended. # (suggestion: saslauthd) NAME="saslauthd" # Which authentication mechanisms should saslauthd use? (default: pam) # # Available options in this Debian package: # getpwent -- use the getpwent() library function # kerberos5 -- use Kerberos 5 # pam -- use PAM # rimap -- use a remote IMAP server # shadow -- use the local shadow password file # sasldb -- use the local sasldb database file # ldap -- use LDAP (configuration is in /etc/saslauthd.conf) # # Only one option may be used at a time. See the saslauthd man page # for more information. # # Example: MECHANISMS="pam" MECHANISMS="pam" # Additional options for this mechanism. (default: none) # See the saslauthd man page for information about mech-specific options. MECH_OPTIONS="" # How many saslauthd processes should we run? (default: 5) # A value of 0 will fork a new process for each connection. THREADS=5 # Other options (default: -c -m /var/run/saslauthd) # Note: You MUST specify the -m option or saslauthd won't run! # # WARNING: DO NOT SPECIFY THE -d OPTION. # The -d option will cause saslauthd to run in the foreground instead of as # a daemon. This will PREVENT YOUR SYSTEM FROM BOOTING PROPERLY. If you wish # to run saslauthd in debug mode, please run it by hand to be safe. # # See /usr/share/doc/sasl2-bin/README.Debian for Debian-specific information. # See the saslauthd man page and the output of 'saslauthd -h' for general # information about these options. # # Example for chroot Postfix users: "-c -m /var/spool/postfix/var/run/saslauthd" # Example for non-chroot Postfix users: "-c -m /var/run/saslauthd" # # To know if your Postfix is running chroot, check /etc/postfix/master.cf. # If it has the line "smtp inet n - y - - smtpd" or "smtp inet n - - - - smtpd" # then your Postfix is running in a chroot. # If it has the line "smtp inet n - n - - smtpd" then your Postfix is NOT # running in a chroot. #OPTIONS="-c -m /var/run/saslauthd" OPTIONS="-c -m /var/spool/postfix/var/run/saslauthd -r" |
Quindi crea il file /etc/pam.d/smtp. Dovrebbe contenere solo le due righe seguenti (assicurati di inserire i dettagli del database corretti):
vi /etc/pam.d/smtp
auth required pam_mysql.so user=mail_admin passwd=mail_admin_password host=127.0.0.1 db=mail table=users usercolumn=email passwdcolumn=password crypt=1 account sufficient pam_mysql.so user=mail_admin passwd=mail_admin_password host=127.0.0.1 db=mail table=users usercolumn=email passwdcolumn=password crypt=1 |
Quindi crea il file /etc/postfix/sasl/smtpd.conf. Dovrebbe assomigliare a questo:
vi /etc/postfix/sasl/smtpd.conf
pwcheck_method: saslauthd mech_list: plain login allow_plaintext: true auxprop_plugin: sql sql_engine: mysql sql_hostnames: 127.0.0.1 sql_user: mail_admin sql_passwd: mail_admin_password sql_database: mail sql_select: select password from users where email = '%[email protected]%r' |
Quindi aggiungi l'utente postfix al gruppo sasl (questo assicura che Postfix abbia il permesso di accedere a saslauthd):
adduser postfix sasl
Quindi riavvia Postfix e Saslauthd:
/etc/init.d/postfix restart
/etc/init.d/saslauthd restart
7 Configura corriere
Ora dobbiamo dire a Courier che dovrebbe autenticarsi sul nostro database MySQL. Per prima cosa, modifica /etc/courier/authdaemonrc e cambia il valore di authmodulelist in modo che legga:
vi /etc/courier/authdaemonrc
[...] authmodulelist="authmysql" [...] |
Quindi fai un backup di /etc/courier/authmysqlrc e svuota il vecchio file:
cp /etc/courier/authmysqlrc /etc/courier/authmysqlrc_orig
cat /dev/null> /etc/courier/authmysqlrc
Quindi apri /etc/courier/authmysqlrc e inserisci le seguenti righe:
vi /etc/courier/authmysqlrc
MYSQL_SERVER localhost MYSQL_USERNAME mail_admin MYSQL_PASSWORD mail_admin_password MYSQL_PORT 0 MYSQL_DATABASE mail MYSQL_USER_TABLE users MYSQL_CRYPT_PWFIELD password #MYSQL_CLEAR_PWFIELD password MYSQL_UID_FIELD 5000 MYSQL_GID_FIELD 5000 MYSQL_LOGIN_FIELD email MYSQL_HOME_FIELD "/home/vmail" MYSQL_MAILDIR_FIELD CONCAT(SUBSTRING_INDEX(email,'@',-1),'/',SUBSTRING_INDEX(email,'@',1),'/') #MYSQL_NAME_FIELD MYSQL_QUOTA_FIELD quota |
Durante l'installazione, i certificati SSL per IMAP-SSL e POP3-SSL vengono creati con il nome host localhost. Per cambiarlo nel nome host corretto (server1.example.com in questo tutorial), elimina i certificati...
cd /etc/courier
rm -f /etc/courier/imapd.pem
rm -f /etc/courier/pop3d.pem
... e modificare i due file seguenti; sostituisci CN=localhost con CN=server1.example.com (puoi anche modificare gli altri valori, se necessario):
vi /etc/courier/imapd.cnf
[...] CN=server1.example.com [...] |
vi /etc/courier/pop3d.cnf
[...] CN=server1.example.com [...] |
Quindi ricrea i certificati...
mkimapdcert
mkpop3dcert
... e riavvia Courier:
/etc/init.d/courier-authdaemon restart
/etc/init.d/courier-imap restart
/etc/init.d/courier-imap-ssl restart
/etc/ init.d/courier-pop restart
/etc/init.d/courier-pop-ssl restart
Eseguendo
telnet localhost pop3
puoi vedere se il tuo server POP3 funziona correttamente. Dovrebbe restituire +OK Salve. (Digita quit per tornare alla shell di Linux.)
[email protected]:/etc/courier# telnet localhost pop3
Tentativo 127.0.0.1...
Connesso a localhost.localdomain.
Il carattere di escape è '^]'.
+OK Salve.
<-- esci
+OK Migliore fortuna la prossima volta.
Connessione chiusa da host straniero.
[email protetta]:/etc/courier#
8 Modifica /etc/aliases
Ora dovremmo aprire /etc/alias. Assicurati che postmaster punti a root e root al tuo nome utente o al tuo indirizzo email, ad es. così:
vi /etc/aliases
[...] postmaster: root root: [email protected] [...] |
o in questo modo (se l'amministratore è il tuo nome utente):
[...] postmaster: root root: administrator [...] |
Ogni volta che modifichi /etc/aliases, devi eseguire
newaliases
in seguito e riavvia Postfix:
/etc/init.d/postfix restart
9 Installa amavisd-new, SpamAssassin e ClamAV
Per installare amavisd-new, spamassassin e clamav, eseguire il comando seguente:
apt-get install amavisd-new spamassassin clamav clamav-daemon zoo unzip bzip2 libnet-ph-perl libnet-snpp-perl libnet-telnet-perl nomarch lzop pax
Successivamente dobbiamo configurare amavisd-new. La configurazione è suddivisa in vari file che risiedono nella directory /etc/amavis/conf.d. Dai un'occhiata a ciascuno di essi per familiarizzare con la configurazione. La maggior parte delle impostazioni va bene, tuttavia dobbiamo modificare tre file:
Per prima cosa dobbiamo abilitare ClamAV e SpamAssassin in /etc/amavis/conf.d/15-content_filter_mode decommentando le righe @bypass_virus_checks_maps e @bypass_spam_checks_maps:
vi /etc/amavis/conf.d/15-content_filter_mode
Il file dovrebbe assomigliare a questo:
use strict; # You can modify this file to re-enable SPAM checking through spamassassin # and to re-enable antivirus checking. # # Default antivirus checking mode # Please note, that anti-virus checking is DISABLED by # default. # If You wish to enable it, please uncomment the following lines: @bypass_virus_checks_maps = ( \%bypass_virus_checks, \@bypass_virus_checks_acl, \$bypass_virus_checks_re); # # Default SPAM checking mode # Please note, that anti-spam checking is DISABLED by # default. # If You wish to enable it, please uncomment the following lines: @bypass_spam_checks_maps = ( \%bypass_spam_checks, \@bypass_spam_checks_acl, \$bypass_spam_checks_re); 1; # ensure a defined return |
E poi dovresti dare un'occhiata alle impostazioni dello spam e alle azioni per spam-/virus-mails in /etc/amavis/conf.d/20-debian_defaults. Non è necessario modificare nulla se le impostazioni predefinite sono ok per te. Il file contiene molte spiegazioni, quindi non è necessario spiegare le impostazioni qui:
vi /etc/amavis/conf.d/20-debian_defaults
[...] $QUARANTINEDIR = "$MYHOME/virusmails"; $quarantine_subdir_levels = 1; # enable quarantine dir hashing $log_recip_templ = undef; # disable by-recipient level-0 log entries $DO_SYSLOG = 1; # log via syslogd (preferred) $syslog_ident = 'amavis'; # syslog ident tag, prepended to all messages $syslog_facility = 'mail'; $syslog_priority = 'debug'; # switch to info to drop debug output, etc $enable_db = 1; # enable use of BerkeleyDB/libdb (SNMP and nanny) $enable_global_cache = 1; # enable use of libdb-based cache if $enable_db=1 $inet_socket_port = 10024; # default listening socket $sa_spam_subject_tag = '***SPAM*** '; $sa_tag_level_deflt = 2.0; # add spam info headers if at, or above that level $sa_tag2_level_deflt = 6.31; # add 'spam detected' headers at that level $sa_kill_level_deflt = 6.31; # triggers spam evasive actions $sa_dsn_cutoff_level = 10; # spam level beyond which a DSN is not sent [...] $final_virus_destiny = D_DISCARD; # (data not lost, see virus quarantine) $final_banned_destiny = D_BOUNCE; # D_REJECT when front-end MTA $final_spam_destiny = D_BOUNCE; $final_bad_header_destiny = D_PASS; # False-positive prone (for spam) [...] |
Infine, modifica /etc/amavis/conf.d/50-user e aggiungi la riga $pax='pax'; nel mezzo:
vi /etc/amavis/conf.d/50-user
use strict; # # Place your configuration directives here. They will override those in # earlier files. # # See /usr/share/doc/amavisd-new/ for documentation and examples of # the directives you can use in this file # $pax='pax'; #------------ Do not modify anything below this line ------------- 1; # ensure a defined return |
Successivamente, esegui questi comandi per aggiungere l'utente clamav al gruppo amavis e riavviare amavisd-new e ClamAV:
adduser clamav amavis
/etc/init.d/amavis restart
/etc/init.d/clamav-freshclam restart
/etc/init.d/clamav-daemon restart
Ora dobbiamo configurare Postfix per reindirizzare la posta in arrivo tramite amavisd-new:
postconf -e 'content_filter =amavis:[127.0.0.1]:10024'
postconf -e 'receive_override_options =no_address_mappings'
Successivamente aggiungi le seguenti righe a /etc/postfix/master.cf:
vi /etc/postfix/master.cf
[...]
amavis unix - - - - 2 smtp
-o smtp_data_done_timeout=1200
-o smtp_send_xforward_command=yes
127.0.0.1:10025 inet n - - - - smtpd
-o content_filter=
-o local_recipient_maps=
-o relay_recipient_maps=
-o smtpd_restriction_classes=
-o smtpd_client_restrictions=
-o smtpd_helo_restrictions=
-o smtpd_sender_restrictions=
-o smtpd_recipient_restrictions=permit_mynetworks,reject
-o mynetworks=127.0.0.0/8
-o strict_rfc821_envelopes=yes
-o receive_override_options=no_unknown_recipient_checks,no_header_body_checks |
Quindi riavvia Postfix:
/etc/init.d/postfix restart
Ora corri
netstat -tap
e dovresti vedere Postfix (master) in ascolto sulla porta 25 (smtp) e 10025 e amavisd-new sulla porta 10024:
[email protetta]:/etc/courier# netstat -tap
Connessioni Internet attive (server e stabilite)
Proto Recv-Q Send-Q Indirizzo locale Indirizzo estero Stato PID/nome del programma
tcp 0 0 *:http *:* LISTEN 6134/apache2
tcp 0 0 *:ssh *:* LISTEN 610/sshd
tcp 0 0 *:smtp *:* LISTEN 23128/master
tcp 0 0 localhost.localdo:10024 *:* LISTEN 21937/amavisd-new (
tcp 0 0 localhost.localdo:10025 *:* LISTEN 23128/master
tcp 0 0 localhost.localdo:mysql * :* LISTEN 4308/mysqld
tcp 0 52 server1.example.com:ssh 192.168.0.206:57597 ESTABLISHED 976/0
tcp6 0 0 [::]:ssh [::]:* LISTEN 610 /sshd
tcp6 0 0 [::]:smtp [::]:* LISTEN 23128/master
tcp6 0 0 [::]:imaps [::]:* LISTEN 18191/couriertcpd
tcp6 0 0 [::]:pop3s [::]:* LISTEN 18259/couriertcpd
tcp6 0 0 [::]:pop3 [::]:* LISTEN 18222/couriertcpd
tcp6 0 0 [::]:imap2 [::]:* LISTEN 18154/couriertcpd
[email protected]:/etc/courier#
10 Install Razor, Pyzor And DCC And Configure SpamAssassin
Razor, Pyzor and DCC are spamfilters that use a collaborative filtering network. To install Razor and Pyzor, run
apt-get install razor pyzor
DCC isn't available in the Ubuntu 12.10 repositories, so we install it as follows:
cd /tmp
wget http://www.dcc-servers.net/dcc/source/dcc-dccproc.tar.Z
tar xzvf dcc-dccproc.tar.Z
cd dcc-dccproc-1.3.143
./configure --with-uid=amavis
make
make install
chown -R amavis:amavis /var/dcc
ln -s /var/dcc/libexec/dccifd /usr/local/bin/dccifd
Now we have to tell SpamAssassin to use these three programs. Edit /etc/spamassassin/local.cf and add the following lines to it:
vi /etc/spamassassin/local.cf
[...] #dcc use_dcc 1 dcc_path /usr/local/bin/dccproc #pyzor use_pyzor 1 pyzor_path /usr/bin/pyzor #razor use_razor2 1 razor_config /etc/razor/razor-agent.conf #bayes use_bayes 1 use_bayes_rules 1 bayes_auto_learn 1 |
Then we must enable the DCC plugin in SpamAssassin. Open /etc/spamassassin/v310.pre and uncomment the loadplugin Mail::SpamAssassin::Plugin::DCC line:
vi /etc/spamassassin/v310.pre
[...] # DCC - perform DCC message checks. # # DCC is disabled here because it is not open source. See the DCC # license for more details. # loadplugin Mail::SpamAssassin::Plugin::DCC [...] |
You can check your SpamAssassin configuration by executing:
spamassassin --lint
It shouldn't show any errors.
Restart amavisd-new afterwards:
/etc/init.d/amavis restart
Now we update our SpamAssassin rulesets as follows:
sa-update --no-gpg
We create a cron job so that the rulesets will be updated regularly. Corri
crontab -e
to open the cron job editor. Create the following cron job:
23 4 */2 * * /usr/bin/sa-update --no-gpg &> /dev/null |
This will update the rulesets every second day at 4.23h.
11 Quota Exceedance Notifications
If you want to get notifications about all the email accounts that are over quota, then create the file /usr/local/sbin/quota_notify:
cd /usr/local/sbin/
vi quota_notify
#!/usr/bin/perl -w
# Author <[email protected]>
#
# This script assumes that virtual_mailbox_base in defined
# in postfix's main.cf file. This directory is assumed to contain
# directories which themselves contain your virtual user's maildirs.
# For example:
#
# -----------/
# |
# |
# home/vmail/domains/
# | |
# | |
# example.com/ foo.com/
# |
# |
# -----------------
# | | |
# | | |
# user1/ user2/ user3/
# |
# |
# maildirsize
#
use strict;
my $POSTFIX_CF = "/etc/postfix/main.cf";
my $MAILPROG = "/usr/sbin/sendmail -t";
my $WARNPERCENT = 80;
my @POSTMASTERS = ('[email protected]');
my $CONAME = 'My Company';
my $COADDR = '[email protected]';
my $SUADDR = '[email protected]';
my $MAIL_REPORT = 1;
my $MAIL_WARNING = 1;
#get virtual mailbox base from postfix config
open(PCF, "< $POSTFIX_CF") or die $!;
my $mboxBase;
while (<PCF>) {
next unless /virtual_mailbox_base\s*=\s*(.*)\s*/;
$mboxBase = $1;
}
close(PCF);
#assume one level of subdirectories for domain names
my @domains;
opendir(DIR, $mboxBase) or die $!;
while (defined(my $name = readdir(DIR))) {
next if $name =~ /^\.\.?$/; #skip '.' and '..'
next unless (-d "$mboxBase/$name");
push(@domains, $name);
}
closedir(DIR);
#iterate through domains for username/maildirsize files
my @users;
chdir($mboxBase);
foreach my $domain (@domains) {
opendir(DIR, $domain) or die $!;
while (defined(my $name = readdir(DIR))) {
next if $name =~ /^\.\.?$/; #skip '.' and '..'
next unless (-d "$domain/$name");
push(@users, {"$name\@$domain" => "$mboxBase/$domain/$name"});
}
}
closedir(DIR);
#get user quotas and percent used
my (%lusers, $report);
foreach my $href (@users) {
foreach my $user (keys %$href) {
my $quotafile = "$href->{$user}/maildirsize";
next unless (-f $quotafile);
open(QF, "< $quotafile") or die $!;
my ($firstln, $quota, $used);
while (<QF>) {
my $line = $_;
if (! $firstln) {
$firstln = 1;
die "Error: corrupt quotafile $quotafile"
unless ($line =~ /^(\d+)S/);
$quota = $1;
last if (! $quota);
next;
}
die "Error: corrupt quotafile $quotafile"
unless ($line =~ /\s*(-?\d+)/);
$used += $1;
}
close(QF);
next if (! $used);
my $percent = int($used / $quota * 100);
$lusers{$user} = $percent unless not $percent;
}
}
#send a report to the postmasters
if ($MAIL_REPORT) {
open(MAIL, "| $MAILPROG");
select(MAIL);
map {print "To: $_\n"} @POSTMASTERS;
print "From: $COADDR\n";
print "Subject: Daily Quota Report.\n";
print "DAILY QUOTA REPORT:\n\n";
print "----------------------------------------------\n";
print "| % USAGE | ACCOUNT NAME |\n";
print "----------------------------------------------\n";
foreach my $luser ( sort { $lusers{$b} <=> $lusers{$a} } keys %lusers ) {
printf("| %3d | %32s |\n", $lusers{$luser}, $luser);
print "---------------------------------------------\n";
}
print "\n--\n";
print "$CONAME\n";
close(MAIL);
}
#email a warning to people over quota
if ($MAIL_WARNING) {
foreach my $luser (keys (%lusers)) {
next unless $lusers{$luser} >= $WARNPERCENT; # skip those under quota
open(MAIL, "| $MAILPROG");
select(MAIL);
print "To: $luser\n";
map {print "BCC: $_\n"} @POSTMASTERS;
print "From: $SUADDR\n";
print "Subject: WARNING: Your mailbox is $lusers{$luser}% full.\n";
print "Reply-to: $SUADDR\n";
print "Your mailbox: $luser is $lusers{$luser}% full.\n\n";
print "Once your e-mail box has exceeded your monthly storage quota\n";
print "your monthly billing will be automatically adjusted.\n";
print "Please consider deleting e-mail and emptying your trash folder to clear some space.\n\n";
print "Contact <$SUADDR> for further assistance.\n\n";
print "Thank You.\n\n";
print "--\n";
print "$CONAME\n";
close(MAIL);
}
} |
Make sure that you adjust the variables at the top (especially the [email protected] email address).
We must make the file executable:
chmod 755 quota_notify
Corri
crontab -e
to create a cron job for that script:
0 0 * * * /usr/local/sbin/quota_notify &> /dev/null |
12 Test Postfix
To see if Postfix is ready for SMTP-AUTH and TLS, run
telnet localhost 25
After you have established the connection to your Postfix mail server type
ehlo localhost
If you see the lines
250-STARTTLS
e
250-AUTH PLAIN LOGIN
everything is fine:
[email protected]:/usr/local/sbin# telnet localhost 25
Trying 127.0.0.1...
Connected to localhost.localdomain.
Escape character is '^]'.
220 server1.example.com ESMTP Postfix (Ubuntu)
<-- ehlo localhost
250-server1.example.com
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-STARTTLS
250-AUTH PLAIN LOGIN
250-AUTH=PLAIN LOGIN
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
<-- quit
221 2.0.0 Bye
Connection closed by foreign host.
[email protected]:/usr/local/sbin#
Type
quit
to return to the system shell.
13 Populate The Database And Test
To populate the database you can use the MySQL shell:
mysql -u root -p
USE mail;
At least you have to create entries in the tables domains and users :
INSERT INTO `domains` (`domain`) VALUES ('example.com');
INSERT INTO `users` (`email`, `password`, `quota`) VALUES ('[email protected]', ENCRYPT('secret'), 10485760);
(Please take care that you use the ENCRYPT syntax in the second INSERT statement in order to encrypt the password!)
If you want to make entries in the other two tables, that would look like this:
INSERT INTO `forwardings` (`source`, `destination`) VALUES ('[email protected]', '[email protected]');
INSERT INTO `transport` (`domain`, `transport`) VALUES ('example.com', 'smtp:mail.example.com');
To leave the MySQL shell, type
quit;
Per la maggior parte delle persone è più facile se hanno un front-end grafico per MySQL; therefore you can also use phpMyAdmin (in this example under http://192.168.0.100/phpmyadmin/ or http://server1.example.com/phpmyadmin/) to administrate the mail database. Again, when you create a user, go sure that you use the ENCRYPT function to encrypt the password:
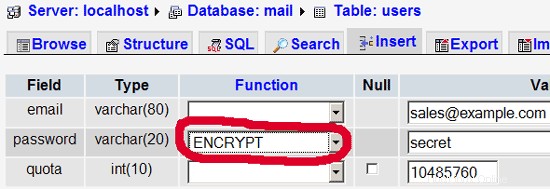
I do not think I have to explain the domains and users table further.
The forwardings table can have entries like the following:
| source | destination | |
| [email protected] | [email protected] | Redirects emails for [email protected] to [email protected] |
| @example.com | [email protected] | Creates a Catch-All account for [email protected] All emails to example.com will arrive at [email protected], except those that exist in the users table (i.e., if [email protected] exists in the users table, mails to [email protected] will still arrive at [email protected]). |
| @example.com | @anotherdomain.tld | This redirects all emails to example.com to the same user at anotherdomain.tld. E.g., emails to thoma[email protected] will be forwarded to [email protected] |
| [email protected] | [email protected], [email protected] | Forward emails for [email protected] to two or more email addresses. All listed email addresses under destination receive a copy of the email. |
The transport table can have entries like these:
| domain | transport | |
| example.com | : | Delivers emails for example.com locally. This is as if this record would not exist in this table at all. |
| example.com | smtp:mail.anotherdomain.tld | Delivers all emails for example.com via smtp to the server mail.anotherdomain.com. |
| example.com | smtp:mail.anotherdomain.tld:2025 | Delivers all emails for example.com via smtp to the server mail.anotherdomain.com, but on port 2025, not 25 which is the default port for smtp. |
| example.com |
smtp:[1.2.3.4] | The square brackets prevent Postfix from doing lookups of the MX DNS record for the address in square brackets. Makes sense for IP addresses. |
| .example.com | smtp:mail.anotherdomain.tld | Mail for any subdomain of example.com is delivered to mail.anotherdomain.tld. |
| * | smtp:mail.anotherdomain.tld | All emails are delivered to mail.anotherdomain.tld. |
| [email protected] | smtp:mail.anotherdomain.tld | Emails for [email protected] are delivered to mail.anotherdomain.tld. |
See
man transport
for more details.
Please keep in mind that the order of entries in the transport table is important! The entries will be followed from the top to the bottom.
Important: Postfix uses a caching mechanism for the transports, therefore it might take a while until you changes in the transport table take effect. If you want them to take effect immediately, run
postfix reload
after you have made your changes in the transport table.
14 Send A Welcome Email For Creating Maildir
When you create a new email account and try to fetch emails from it (with POP3/IMAP) you will probably get error messages saying that the Maildir doesn't exist. The Maildir is created automatically when the first email arrives for the new account. Therefore it's a good idea to send a welcome email to a new account.
First, we install the mailx package:
apt-get install mailutils
To send a welcome email to [email protected], we do this:
mailx [email protected]
You will be prompted for the subject. Type in the subject (e.g. Welcome), then press ENTER, and in the next line type your message. When the message is finished, press ENTER again so that you are in a new line, then press CTRL+D; if you don't want to cc the mail, press ENTER again:
[email protected]:/usr/local/sbin# mailx [email protected]
Cc:<-- ENTER
Subject:Welcome <-- ENTER
Welcome! Have fun with your new mail account. <-- ENTER
<-- CTRL+D
[email protected]:/usr/local/sbin#
15 Installing SquirrelMail
SquirrelMail is a webmail interface that will let your users send and receive emails in a browser. This chapter shows how to install it and adjust it to our setup so that users can even change their email account password from the SquirrelMail interface.
To install SquirrelMail, we run:
apt-get install squirrelmail squirrelmail-compatibility php-pear php-db
Next we symlink the Apache configuration that comes with the SquirrelMail package to the /etc/apache2/conf.d directory and restart Apache:
ln -s /etc/squirrelmail/apache.conf /etc/apache2/conf.d/squirrelmail.conf
/etc/init.d/apache2 restart
SquirrelMail comes with some pre-installed plugins, unfortunately none of them is capable of letting us change our email password in our MySQL database. But there's the Change SQL Password plugin which we can install manually:
cd /usr/share/squirrelmail/plugins
wget http://www.squirrelmail.org/plugins/change_sqlpass-3.3-1.2.tar.gz
tar xvfz change_sqlpass-3.3-1.2.tar.gz
cd change_sqlpass
cp config.php.sample config.php
Now we must edit config.php and adjust it to our setup. Please adjust the $csp_dsn, $lookup_password_query, $password_update_queries, $password_encryption, $csp_salt_static, and $csp_delimiter variables as follows and comment out $csp_salt_query:
vi config.php
[...]
$csp_dsn = 'mysql://mail_admin:[email protected]/mail';
[...]
$lookup_password_query = 'SELECT count(*) FROM users WHERE email = "%1" AND password = %4';
[...]
$password_update_queries = array('UPDATE users SET password = %4 WHERE email = "%1"');
[...]
$password_encryption = 'MYSQLENCRYPT';
[...]
$csp_salt_static = 'LEFT(password, 2)';
[...]
//$csp_salt_query = 'SELECT salt FROM users WHERE username = "%1"';
[...]
$csp_delimiter = '@';
[...] |
The complete file looks as follows:
<?php
/**
* SquirrelMail Change SQL Password Plugin
* Copyright (C) 2001-2002 Tyler Akins
* 2002 Thijs Kinkhorst <[email protected]>
* 2002-2005 Paul Lesneiwski <[email protected]>
* This program is licensed under GPL. See COPYING for details
*
* @package plugins
* @subpackage Change SQL Password
*
*/
// Global Variables, don't touch these unless you want to break the plugin
//
global $csp_dsn, $password_update_queries, $lookup_password_query,
$force_change_password_check_query, $password_encryption,
$csp_salt_query, $csp_salt_static, $csp_secure_port,
$csp_non_standard_http_port, $csp_delimiter, $csp_debug,
$min_password_length, $max_password_length, $include_digit_in_password,
$include_uppercase_letter_in_password, $include_lowercase_letter_in_password,
$include_nonalphanumeric_in_password;
// csp_dsn
//
// Theoretically, any SQL database supported by Pear should be supported
// here. The DSN (data source name) must contain the information needed
// to connect to your database backend. A MySQL example is included below.
// For more details about DSN syntax and list of supported database types,
// please see:
// http://pear.php.net/manual/en/package.database.db.intro-dsn.php
//
//$csp_dsn = 'mysql://user:[email protected]/email_users';
$csp_dsn = 'mysql://mail_admin:[email protected]/mail';
// lookup_password_query
//
// This plugin will always verify the user's old password
// against their login password, but an extra check can also
// be done against the database for more security if you
// desire. If you do not need the extra password check,
// make sure this setting is empty.
//
// This is a query that returns a positive value if a user
// and password pair are found in the database.
//
// This query should return one value (one row, one column), the
// value being ideally a one or a zero, simply indicating that
// the user/password pair does in fact exist in the database.
//
// %1 in this query will be replaced with the full username
// (including domain), such as "[email protected]"
// %2 in this query will be replaced with the username (without
// any domain portion), such as "jose"
// %3 in this query will be replaced with the domain name,
// such as "example.com"
// %4 in this query will be replaced with the current (old)
// password in whatever encryption format is needed per other
// plugin configuration settings (Note that the syntax of
// the password will be provided depending on your encryption
// choices, so you NEVER need to provide quotes around this
// value in the query here.)
// %5 in this query will be replaced with the current (old)
// password in unencrypted plain text. If you do not use any
// password encryption, %4 and %5 will be the same values,
// except %4 will have double quotes around it and %5 will not.
//
//$lookup_password_query = '';
// TERRIBLE SECURITY: $lookup_password_query = 'SELECT count(*) FROM users WHERE username = "%1" AND plain_password = "%5"';
//$lookup_password_query = 'SELECT count(*) FROM users WHERE username = "%1" AND crypt_password = %4';
$lookup_password_query = 'SELECT count(*) FROM users WHERE email = "%1" AND password = %4';
// password_update_queries
//
// An array of SQL queries that will all be executed
// whenever a password change attempt is made.
//
// Any number of queries may be included here.
// The queries will be executed in the order given here.
//
// %1 in all queries will be replaced with the full username
// (including domain), such as "[email protected]"
// %2 in all queries will be replaced with the username (without
// any domain portion), such as "jose"
// %3 in all queries will be replaced with the domain name,
// such as "example.com"
// %4 in all queries will be replaced with the new password
// in whatever encryption format is needed per other
// plugin configuration settings (Note that the syntax of
// the password will be provided depending on your
// encryption choices, so you NEVER need to provide quotes
// around this value in the queries here.)
// %5 in all queries will be replaced with the new password
// in unencrypted plain text - BEWARE! If you do not use
// any password encryption, %4 and %5 will be the same
// values, except %4 will have double quotes around it
// and %5 will not.
//
// $password_update_queries = array(
// 'UPDATE users SET crypt_password = %4 WHERE username = "%1"',
// 'UPDATE user_flags SET force_change_pwd = 0 WHERE username = "%1"',
// 'UPDATE users SET crypt_password = %4, force_change_pwd = 0 WHERE username = "%1"',
// );
$password_update_queries = array('UPDATE users SET password = %4 WHERE email = "%1"');
// force_change_password_check_query
//
// A query that checks for a flag that indicates if a user
// should be forced to change their password. This query
// should return one value (one row, one column) which is
// zero if the user does NOT need to change their password,
// or one if the user should be forced to change it now.
//
// This setting should be an empty string if you do not wish
// to enable this functionality.
//
// %1 in this query will be replaced with the full username
// (including domain), such as "[email protected]"
// %2 in this query will be replaced with the username (without
// any domain portion), such as "jose"
// %3 in this query will be replaced with the domain name,
// such as "example.com"
//
//$force_change_password_check_query = 'SELECT IF(force_change_pwd = "yes", 1, 0) FROM users WHERE username = "%1"';
//$force_change_password_check_query = 'SELECT force_change_pwd FROM users WHERE username = "%1"';
$force_change_password_check_query = '';
// password_encryption
//
// What encryption method do you use to store passwords
// in your database? Please use one of the following,
// exactly as you see it:
//
// NONE Passwords are stored as plain text only
// MYSQLPWD Passwords are stored using the MySQL password() function
// MYSQLENCRYPT Passwords are stored using the MySQL encrypt() function
// PHPCRYPT Passwords are stored using the PHP crypt() function
// MD5CRYPT Passwords are stored using encrypted MD5 algorithm
// MD5 Passwords are stored as MD5 hash
//
//$password_encryption = 'MYSQLPWD';
$password_encryption = 'MYSQLENCRYPT';
// csp_salt_query
// csp_salt_static
//
// Encryption types that need a salt need to know where to get
// that salt. If you have a constant, known salt value, you
// should define it in $csp_salt_static. Otherwise, leave that
// value empty and define a value for the $csp_salt_query.
//
// Leave both values empty if you do not need (or use) salts
// to encrypt your passwords.
//
// The query should return one value (one row, one column) which
// is the salt value for the current user's password. This
// query is ignored if $csp_salt_static is anything but empty.
//
// %1 in this query will be replaced with the full username
// (including domain), such as "[email protected]"
// %2 in this query will be replaced with the username (without
// any domain portion), such as "jose"
// %3 in this query will be replaced with the domain name,
// such as "example.com"
//
//$csp_salt_static = 'LEFT(crypt_password, 2)';
//$csp_salt_static = '"a4"'; // use this format with MYSQLENCRYPT
//$csp_salt_static = '$2$blowsomefish$'; // use this format with PHPCRYPT
//$csp_salt_static = '';
$csp_salt_static = 'LEFT(password, 2)';
//$csp_salt_query = 'SELECT SUBSTRING_INDEX(crypt_password, '$', 1) FROM users WHERE username = "%1"';
//$csp_salt_query = 'SELECT SUBSTRING(crypt_password, (LENGTH(SUBSTRING_INDEX(crypt_password, '$', 2)) + 2)) FROM users WHERE username = "%1"';
//$csp_salt_query = 'SELECT salt FROM users WHERE username = "%1"';
//$csp_salt_query = '';
// csp_secure_port
//
// You may ensure that SSL encryption is used during password
// change by setting this to the port that your HTTPS is served
// on (443 is typical). Set to zero if you do not wish to force
// an HTTPS connection when users are changing their passwords.
//
// You may override this value for certain domains, users, or
// service levels through the Virtual Host Login (vlogin) plugin
// by setting a value(s) for $vlogin_csp_secure_port in the vlogin
// configuration.
//
$csp_secure_port = 0;
//$csp_secure_port = 443;
// csp_non_standard_http_port
//
// If you serve standard HTTP web requests on a non-standard
// port (anything other than port 80), you should specify that
// port number here. Set to zero otherwise.
//
// You may override this value for certain domains, users, or
// service levels through the Virtual Host Login (vlogin) plugin
// by setting a value(s) for $vlogin_csp_non_standard_http_port
// in the vlogin configuration.
//
//$csp_non_standard_http_port = 8080;
$csp_non_standard_http_port = 0;
// min_password_length
// max_password_length
// include_digit_in_password
// include_uppercase_letter_in_password
// include_lowercase_letter_in_password
// include_nonalphanumeric_in_password
//
// You can set the minimum and maximum password lengths that
// you accept or leave those settings as zero to indicate that
// no limit should be applied.
//
// Turn on any of the other settings here to check that the
// new password contains at least one digit, upper case letter,
// lower case letter and/or one non-alphanumeric character.
//
$min_password_length = 6;
$max_password_length = 0;
$include_digit_in_password = 0;
$include_uppercase_letter_in_password = 0;
$include_lowercase_letter_in_password = 0;
$include_nonalphanumeric_in_password = 0;
// csp_delimiter
//
// if your system has usernames with something other than
// an "@" sign separating the user and domain portion,
// specify that character here
//
//$csp_delimiter = '|';
$csp_delimiter = '@';
// debug mode
//
$csp_debug = 0;
?> |
Now we must go into the SquirrelMail configuration and tell SquirrelMail that we use Courier as our POP3 and IMAP server and enable the Change SQL Password and the Compatibility plugins:
/usr/sbin/squirrelmail-configure
You'll see the following menu. Navigate through it as indicated:
SquirrelMail Configuration : Read: config.php (1.4.0)
---------------------------------------------------------
Main Menu --
1. Organization Preferences
2. Server Settings
3. Folder Defaults
4. General Options
5. Themes
6. Address Books
7. Message of the Day (MOTD)
8. Plugins
9. Database
10. Languages
D. Set pre-defined settings for specific IMAP servers
C Turn color on
S Save data
Q Quit
Command >> <-- D
SquirrelMail Configuration : Read: config.php
---------------------------------------------------------
While we have been building SquirrelMail, we have discovered some
preferences that work better with some servers that don't work so
well with others. If you select your IMAP server, this option will
set some pre-defined settings for that server.
Please note that you will still need to go through and make sure
everything is correct. This does not change everything. There are
only a few settings that this will change.
Please select your IMAP server:
bincimap = Binc IMAP server
courier = Courier IMAP server
cyrus = Cyrus IMAP server
dovecot = Dovecot Secure IMAP server
exchange = Microsoft Exchange IMAP server
hmailserver = hMailServer
macosx = Mac OS X Mailserver
mercury32 = Mercury/32
uw = University of Washington's IMAP server
gmail = IMAP access to Google mail (Gmail) accounts
quit = Do not change anything
Command >> <-- courier
imap_server_type = courier
default_folder_prefix = INBOX.
trash_folder = Trash
sent_folder = Sent
draft_folder = Drafts
show_prefix_option = false
default_sub_of_inbox = false
show_contain_subfolders_option = false
optional_delimiter = .
delete_folder = true
Press enter to continue... <-- press ENTER
SquirrelMail Configuration : Read: config.php (1.4.0)
---------------------------------------------------------
Main Menu --
1. Organization Preferences
2. Server Settings
3. Folder Defaults
4. General Options
5. Themes
6. Address Books
7. Message of the Day (MOTD)
8. Plugins
9. Database
10. Languages
D. Set pre-defined settings for specific IMAP servers
C Turn color on
S Save data
Q Quit
Command >> <-- 8
SquirrelMail Configuration : Read: config.php (1.4.0)
---------------------------------------------------------
Plugins
Installed Plugins
1. view_as_html
Available Plugins:
2. administrator
3. bug_report
4. calendar
5. change_sqlpass
6. compatibility
7. delete_move_next
8. demo
9. filters
10. fortune
11. info
12. listcommands
13. mail_fetch
14. message_details
15. newmail
16. sent_subfolders
17. spamcop
18. squirrelspell
19. test
20. translate
R Return to Main Menu
C Turn color on
S Save data
Q Quit
Command >> <-- 6 (or whatever number the compatibility plugin has - it's needed by the change_sqlpass plugin)
SquirrelMail Configuration : Read: config.php (1.4.0)
---------------------------------------------------------
Plugins
Installed Plugins
1. view_as_html
2. compatibility
Available Plugins:
3. administrator
4. bug_report
5. calendar
6. change_sqlpass
7. delete_move_next
8. demo
9. filters
10. fortune
11. info
12. listcommands
13. mail_fetch
14. message_details
15. newmail
16. sent_subfolders
17. spamcop
18. squirrelspell
19. test
20. translate
R Return to Main Menu
C Turn color on
S Save data
Q Quit
Command >> <-- 6 (the number of the change_sqlpass plugin)
SquirrelMail Configuration : Read: config.php (1.4.0)
---------------------------------------------------------
Plugins
Installed Plugins
1. view_as_html
2. compatibility
3. change_sqlpass
Available Plugins:
4. administrator
5. bug_report
6. calendar
7. delete_move_next
8. demo
9. filters
10. fortune
11. info
12. listcommands
13. mail_fetch
14. message_details
15. newmail
16. sent_subfolders
17. spamcop
18. squirrelspell
19. test
20. translate
R Return to Main Menu
C Turn color on
S Save data
Q Quit
Command >> <-- S
SquirrelMail Configuration : Read: config.php (1.4.0)
---------------------------------------------------------
Plugins
Installed Plugins
1. view_as_html
2. compatibility
3. change_sqlpass
Available Plugins:
4. administrator
5. bug_report
6. calendar
7. delete_move_next
8. demo
9. filters
10. fortune
11. info
12. listcommands
13. mail_fetch
14. message_details
15. newmail
16. sent_subfolders
17. spamcop
18. squirrelspell
19. test
20. translate
R Return to Main Menu
C Turn color on
S Save data
Q Quit
Command >> S
Data saved in config.php
Press enter to continue... <-- press ENTER
SquirrelMail Configuration : Read: config.php (1.4.0)
---------------------------------------------------------
Plugins
Installed Plugins
1. view_as_html
2. compatibility
3. change_sqlpass
Available Plugins:
4. administrator
5. bug_report
6. calendar
7. delete_move_next
8. demo
9. filters
10. fortune
11. info
12. listcommands
13. mail_fetch
14. message_details
15. newmail
16. sent_subfolders
17. spamcop
18. squirrelspell
19. test
20. translate
R Return to Main Menu
C Turn color on
S Save data
Q Quit
Command >> <-- Q
Now you can type in http://server1.example.com/squirrelmail or http://192.168.0.100/squirrelmail in your browser to access SquirrelMail.
Log in with your email address (e.g. [email protected]) and your password:
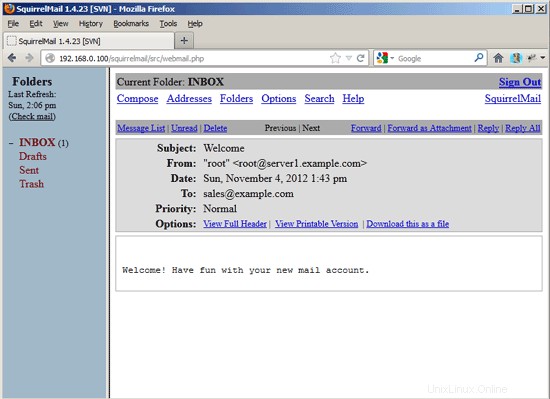
You should find the welcome email in your inbox:
To change your password, go to Options and then select Change Password:
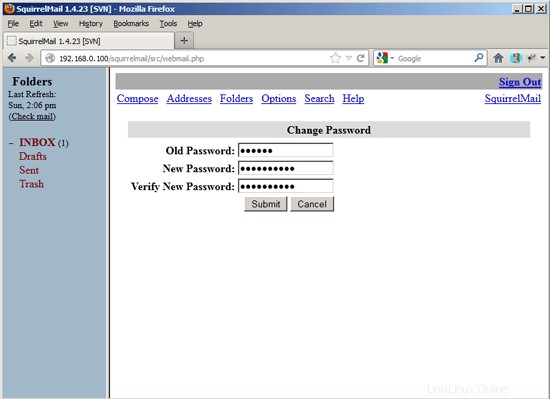
Type in your current password and then your new password twice:
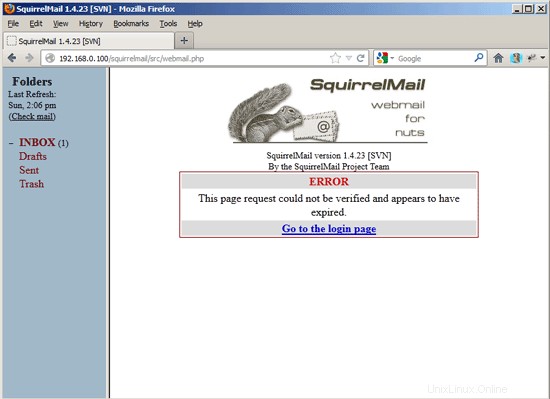
If the password has been changed successfully, you will see the following error message which means you must log in again with your new password (because the old one isn't active anymore):
16 VMA (Virtual Mail Admin Interface)
Virtual Mail Admin (VMA) is a small PHP-based web app written to manage the email system set up in this guide. I didn't test it, but I thought I'd share.
This is what the developer (Charl Loubser) wrote to me in an email:
"Hi There,
I don't know if you'll like this, or if this has any use to you, but I thought I'd Share:
I wrote a silly little webapp for the setup you did in the Howto:https://www.howtoforge.com/virtual-users-domains-postfix-courier-mysql-squirrelmail-ubuntu-10.04
If you approve and think it worthy of sharing on your tutorial, you are more than welcome, and can feel free to do so.
As mentioned in the readme, this is not a perfect app, but it does the job for now, and I'd thing it's relatively safe in a closed environment (LAN setup between servers).
The rar file with the app is attached, but can also be downloaded at :http://code.google.com/p/vma/"
17 References
- Tutorial:ISP-style Email Service with Debian-Sarge and Postfix 2.1:http://workaround.org/articles/ispmail-sarge/
- Postfix + Quota:http://vhcs.net/new/modules/newbb/viewtopic.php?topic_id=3496&forum=17
- Mail Passwords Encrypted using saslauthd:http://www.syscp.de/docs/public/contrib/cryptedmailpws
18 Links
- Postfix MTA:http://www.postfix.org/
- Postfix Quota Patch:http://web.onda.com.br/nadal/
- phpMyAdmin:http://www.phpmyadmin.net/
- SquirrelMail:http://www.squirrelmail.org/
- Ubuntu:http://www.ubuntu.com/
- Virtual Mail Admin Interface (VMA):http://code.google.com/p/vma/