A partire dalla versione 4.0, Samba è in grado di funzionare come controller di dominio (DC) di Active Directory (AD). In questo tutorial, ti mostrerò come configurare Samba 4 come controller di dominio con client Windows 10, CentOS 7 e CentOS 6.
In questo tutorial, compilerò Samba 4 dal sorgente. Se stai cercando un'installazione basata su Samba 4 RPM e una configurazione SELinux per Samba 4, consulta il mio nuovo tutorial su Samba 4 qui.
Utilizzerò 3 sistemi, un server CentOS 7 e un client Windows 10 per la gestione remota, un client CentOS 7 e CentOS 6.
- 192.168.1.190 Samba4 AD centos7
- 192.168.1.191 gestione remota vince 10
- 192.168.1.22 - Autenticazione client - centos 7
- 192.168.1.192 - Autenticazione client - centos 6
Installazione di Samba 4
192.168.1.190 Samba4 AD centos 7
Basis è un CentOS 7 con un'installazione minima e SELinux disabilitato.
[[email protected] ~]# sestatus
SELinux status: disabled
[[email protected] ~]#
Crea una voce nel file /etc/hosts.
[[email protected] ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.1.190 samba4.sunil.cc samba4
[[email protected] ~]#
Installa il repository epel.
[[email protected] ~]# yum install epel-release -y
Installa tutti i pacchetti necessari per compilare samba4.
[[email protected] ~]# yum install perl gcc libacl-devel libblkid-devel gnutls-devel readline-devel python-devel gdb pkgconfig krb5-workstation zlib-devel setroubleshoot-server libaio-devel setroubleshoot-plugins\ policycoreutils-python libsemanage-python setools-libs-python setools-libs popt-devel libpcap-devel sqlite-devel libidn-devel libxml2-devel libacl-devel libsepol-devel libattr-devel keyutils-libs-devel\ cyrus-sasl-devel cups-devel bind-utils libxslt docbook-style-xsl openldap-devel pam-devel bzip2 vim wget -y
Ora scarica il pacchetto samba4. Uso samba-4.6.0 che è l'ultimo durante questa configurazione.
[[email protected] ~]# wget https://download.samba.org/pub/samba/stable/samba-4.6.0.tar.gz
Ora installiamo samba4.
[[email protected] ~]# tar -zxvf samba-4.6.0.tar.gz [[email protected] ~]# cd samba-4.6.0 [[email protected] samba-4.6.0]# ./configure --enable-debug --enable-selftest --with-ads --with-systemd --with-winbind [[email protected] samba-4.6.0]# make && make install
L'installazione richiederà circa 10 minuti a seconda della velocità del sistema.
Ora faremo il provisioning del dominio.
[[email protected] samba]# samba-tool domain provision --use-rfc2307 --interactive
Realm [SUNIL.CC]:
Domain [SUNIL]:
Server Role (dc, member, standalone) [dc]: dc
DNS backend (SAMBA_INTERNAL, BIND9_FLATFILE, BIND9_DLZ, NONE) [SAMBA_INTERNAL]:
DNS forwarder IP address (write 'none' to disable forwarding) [4.2.2.1]:
Administrator password:
Retype password:
Looking up IPv4 addresses
Looking up IPv6 addresses
No IPv6 address will be assigned
Setting up share.ldb
Setting up secrets.ldb
Setting up the registry
Setting up the privileges database
Setting up idmap db
Setting up SAM db
Setting up sam.ldb partitions and settings
Setting up sam.ldb rootDSE
Pre-loading the Samba 4 and AD schema
Adding DomainDN: DC=sunil,DC=cc
Adding configuration container
Setting up sam.ldb schema
Setting up sam.ldb configuration data
Setting up display specifiers
Modifying display specifiers
Adding users container
Modifying users container
Adding computers container
Modifying computers container
Setting up sam.ldb data
Setting up well known security principals
Setting up sam.ldb users and groups
ERROR(ldb): uncaught exception - operations error at ../source4/dsdb/samdb/ldb_modules/password_hash.c:2820
File "/usr/local/samba/lib64/python2.7/site-packages/samba/netcmd/__init__.py", line 176, in _run
return self.run(*args, **kwargs)
File "/usr/local/samba/lib64/python2.7/site-packages/samba/netcmd/domain.py", line 471, in run
nosync=ldap_backend_nosync, ldap_dryrun_mode=ldap_dryrun_mode)
File "/usr/local/samba/lib64/python2.7/site-packages/samba/provision/__init__.py", line 2175, in provision
skip_sysvolacl=skip_sysvolacl)
File "/usr/local/samba/lib64/python2.7/site-packages/samba/provision/__init__.py", line 1787, in provision_fill
next_rid=next_rid, dc_rid=dc_rid)
File "/usr/local/samba/lib64/python2.7/site-packages/samba/provision/__init__.py", line 1447, in fill_samdb
"KRBTGTPASS_B64": b64encode(krbtgtpass.encode('utf-16-le'))
File "/usr/local/samba/lib64/python2.7/site-packages/samba/provision/common.py", line 55, in setup_add_ldif
ldb.add_ldif(data, controls)
File "/usr/local/samba/lib64/python2.7/site-packages/samba/__init__.py", line 225, in add_ldif
self.add(msg, controls)
[[email protected] samba]# Si verificheranno degli errori durante il provisioning del dominio.
Per risolverli, commenta la riga sottostante in /etc/krb5.conf.
-------- #includedir /etc/krb5.conf.d/ --------
Esegui nuovamente il provisioning del dominio e ora il dominio verrà creato senza errori.
[[email protected] etc]# samba-tool domain provision --use-rfc2307 --interactive Realm [SUNIL.CC]: Domain [SUNIL]: Server Role (dc, member, standalone) [dc]: DNS backend (SAMBA_INTERNAL, BIND9_FLATFILE, BIND9_DLZ, NONE) [SAMBA_INTERNAL]: DNS forwarder IP address (write 'none' to disable forwarding) [4.2.2.1]: Administrator password: Retype password: Looking up IPv4 addresses Looking up IPv6 addresses No IPv6 address will be assigned Setting up secrets.ldb Setting up the registry Setting up the privileges database Setting up idmap db Setting up SAM db Setting up sam.ldb partitions and settings Setting up sam.ldb rootDSE Pre-loading the Samba 4 and AD schema Adding DomainDN: DC=sunil,DC=cc Adding configuration container Setting up sam.ldb schema Setting up sam.ldb configuration data Setting up display specifiers Modifying display specifiers Adding users container Modifying users container Adding computers container Modifying computers container Setting up sam.ldb data Setting up well known security principals Setting up sam.ldb users and groups Setting up self join Adding DNS accounts Creating CN=MicrosoftDNS,CN=System,DC=sunil,DC=cc Creating DomainDnsZones and ForestDnsZones partitions Populating DomainDnsZones and ForestDnsZones partitions Setting up sam.ldb rootDSE marking as synchronized Fixing provision GUIDs A Kerberos configuration suitable for Samba AD has been generated at /usr/local/samba/private/krb5.conf Setting up fake yp server settings Once the above files are installed, your Samba4 server will be ready to use Server Role: active directory domain controller Hostname: samba4 NetBIOS Domain: SUNIL DNS Domain: sunil.cc DOMAIN SID: S-1-5-21-2936486394-2075362935-551615353 [[email protected] etc]#
Assicurati che le porte siano aperte nel firewall.
[[email protected] etc]#firewall-cmd --add-port=53/tcp --permanent;firewall-cmd --add-port=53/udp --permanent;firewall-cmd --add-port=88/tcp --permanent;firewall-cmd --add-port=88/udp --permanent; \ firewall-cmd --add-port=135/tcp --permanent;firewall-cmd --add-port=137-138/udp --permanent;firewall-cmd --add-port=139/tcp --permanent; \ firewall-cmd --add-port=389/tcp --permanent;firewall-cmd --add-port=389/udp --permanent;firewall-cmd --add-port=445/tcp --permanent; \ firewall-cmd --add-port=464/tcp --permanent;firewall-cmd --add-port=464/udp --permanent;firewall-cmd --add-port=636/tcp --permanent; \ firewall-cmd --add-port=1024-5000/tcp --permanent;firewall-cmd --add-port=3268-3269/tcp --permanent [[email protected] ~]# firewall-cmd --reload
Crea uno script di avvio per avviare automaticamente il servizio durante il riavvio.
[[email protected] ~]# cat /etc/systemd/system/samba.service [Unit] Description= Samba 4 Active Directory After=syslog.target After=network.target [Service] Type=forking PIDFile=/usr/local/samba/var/run/samba.pid ExecStart=/usr/local/samba/sbin/samba [Install] WantedBy=multi-user.target [[email protected] ~]# [[email protected] ~]# systemctl enable samba Created symlink from /etc/systemd/system/multi-user.target.wants/samba.service to /etc/systemd/system/samba.service. [[email protected] ~]# systemctl start samba
Aggiunta dell'host Windows al dominio
192.168.1.191 gestione remota vince 10
Assicurati che l'host sia stato aggiunto con un indirizzo IP statico.
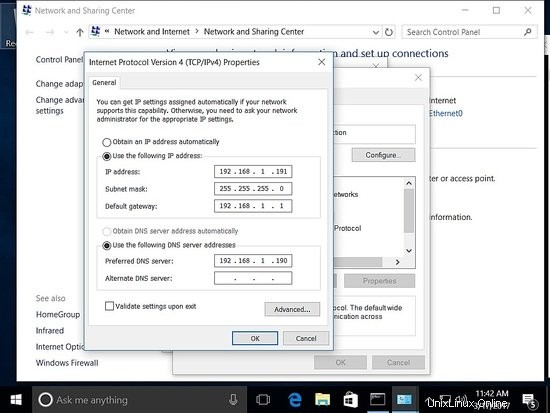
Aggiunta dell'host al dominio.
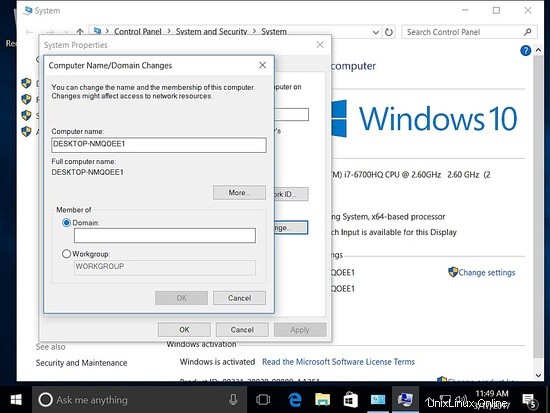
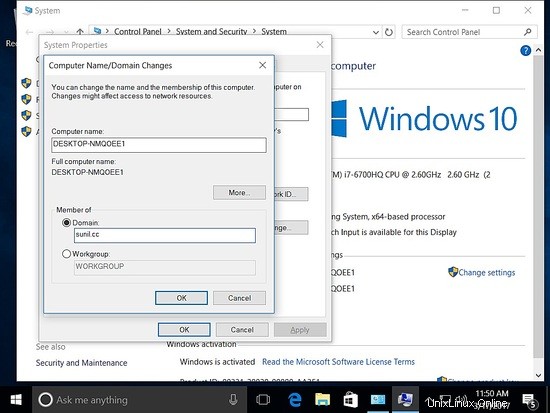
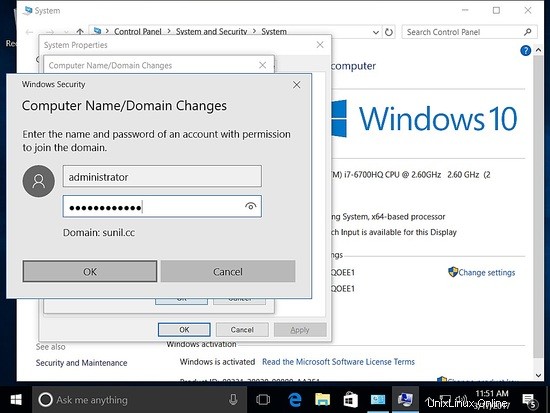
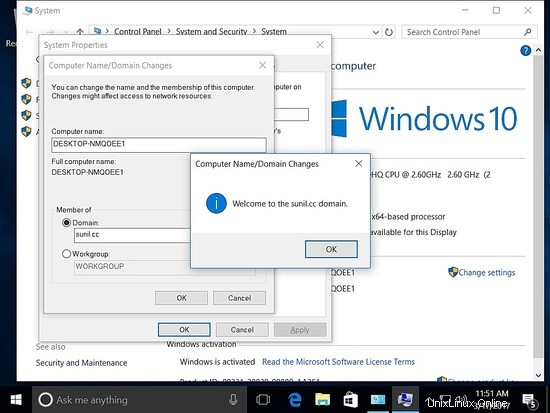
Per gestire Samba4 da Windows, dobbiamo avere installato Microsoft Remote Server Tools (RSAT).
La pagina wiki ha i link https://wiki.samba.org/index.php/Installing_RSAT
Installazione dello strumento RSAT in Windows 10
Esegui il programma di installazione.
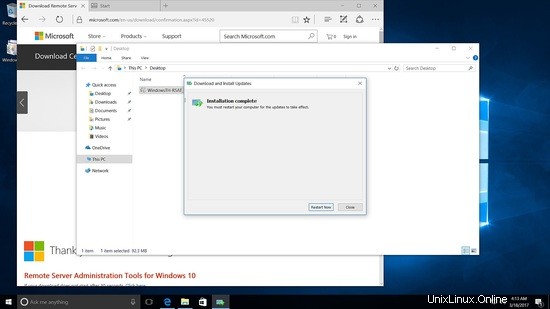
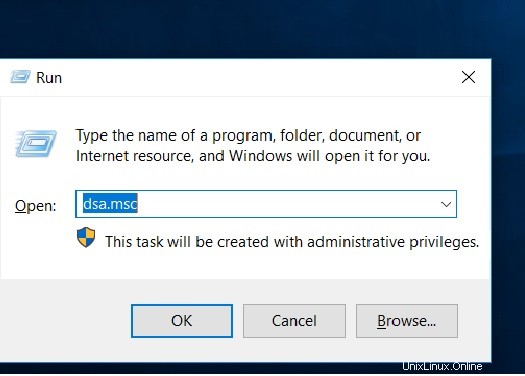
Dopo il riavvio, vai a correre e digita dsa.msc
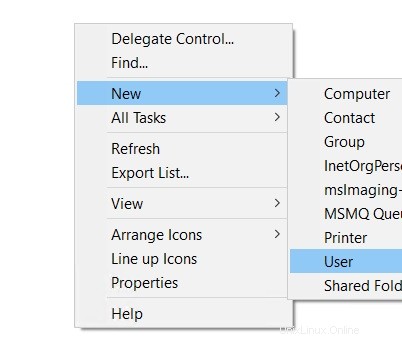
Fai clic su dominio sunil.cc e fai clic con il pulsante destro del mouse su nuovo -> Utenti.
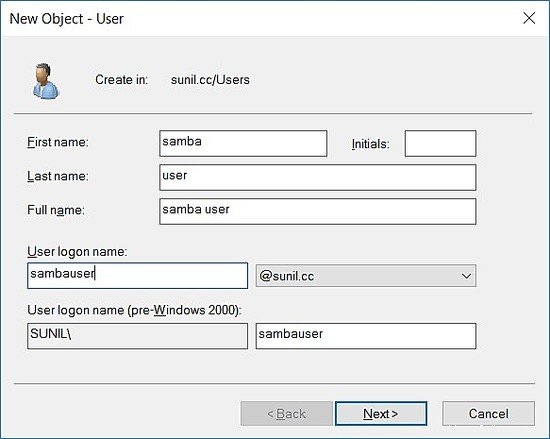
Creazione di un utente di prova.
Autenticazione client con Samba 4 su CentOS 7
192.168.1.22 - Autenticazione client su CentOS 7
Installazione dei pacchetti:
[[email protected] ~]# yum -y install realmd sssd oddjob oddjob-mkhomedir adcli samba-common
Verifica la connettività con samba4:
[[email protected] ~]# realm discover SUNIL.CC sunil.cc type: kerberos realm-name: SUNIL.CC domain-name: sunil.cc configured: kerberos-member server-software: active-directory client-software: sssd required-package: oddjob required-package: oddjob-mkhomedir required-package: sssd required-package: adcli required-package: samba-common-tools login-formats: %U login-policy: allow-realm-logins [[email protected] ~]#
Entrare a far parte del dominio.
[[email protected] ~]# realm join SUNIL.CC Password for Administrator: [[email protected] ~]#
Controlla se siamo in grado di ottenere l'utente da samba4.
[[email protected] ~]# id SUNIL\\testuser uid=1570001104([email protected]) gid=1570000513(domain [email protected]) groups=1570000513(domain [email protected]) [[email protected] ~]#
Configura sssd.
[[email protected] ~]# cat /etc/sssd/sssd.conf [sssd] domains = sunil.cc config_file_version = 2 services = nss, pam [domain/sunil.cc] ad_domain = sunil.cc krb5_realm = SUNIL.CC realmd_tags = manages-system joined-with-samba cache_credentials = True id_provider = ad krb5_store_password_if_offline = True default_shell = /bin/bash ldap_id_mapping = True use_fully_qualified_names = True fallback_homedir = /home/%[email protected]%d access_provider = ad [[email protected] ~]#
Riavvia sssd.
[[email protected] ~]# systemctl restart sssd [[email protected] ~]# systemctl enable sssd
Controlla l'utente.
[[email protected] ~]# id [email protected] uid=1570001105([email protected]) gid=1570000513(domain [email protected]) groups=1570000513(domain [email protected]),1570000512(domain [email protected]),1570000572(denied rodc password replication [email protected]) [[email protected] ~]#
Per ottenere l'utente senza nome di dominio.
[[email protected] ~]# vim /etc/sssd/sssd.conf ----------- ------------ use_fully_qualified_names = False ----------- -----------
Riavvia sssd e controlla il comando id.
[[email protected] ~]# systemctl restart sssd [[email protected] ~]# id sambauser uid=1570001105(sambauser) gid=1570000513(domain users) groups=1570000513(domain users),1570000512(domain admins),1570000572(denied rodc password replication group) [[email protected] ~]#
Autenticazione client con Samba 4 su CentOS 6
192.168.1.192 - Autenticazione client su CentOS 6.
Installazione dei pacchetti.
[[email protected] db]# yum install pam pam_ldap pam_krb5 sssd sssd-ldap sssd-common authconfig oddjob oddjob-mkhomedir openldap openldap-clients krb5-workstation adcli -y
Modifica il file di configurazione di Kerberos.
[[email protected] db]# cat /etc/krb5.conf
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
default_realm = SUNIL.CC
dns_lookup_realm = false
dns_lookup_kdc = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
[realms]
SUNIL.CC = {
kdc = samba4.sunil.cc
admin_server = samba4.sunil.cc
}
[domain_realm]
.sunil.cc = SUNIL.CC
sunil.cc = SUNIL.CC
[[email protected] db]#
Useremo il comando adcli per entrare nel dominio.
[[email protected] db]# adcli info sunil.cc [domain] domain-name = sunil.cc domain-short = SUNIL domain-forest = sunil.cc domain-controller = samba4.sunil.cc domain-controller-site = Default-First-Site-Name domain-controller-flags = pdc gc ldap ds kdc timeserv closest writable good-timeserv full-secret domain-controller-usable = yes domain-controllers = samba4.sunil.cc [computer] computer-site = Default-First-Site-Name [[email protected] db]# [[email protected] db]# adcli join sunil.cc Password for [email protected]: [[email protected] db]#
Assicurati che il biglietto Kerberos sia stato creato.
[[email protected] db]# klist -ke
Configura l'autenticazione.
[[email protected] db]# authconfig --enablesssd --enablesssdauth --enablemkhomedir --update
Modifica ora la configurazione sssd per eseguire l'autenticazione.
[[email protected] db]# cat /etc/sssd/sssd.conf [sssd] services = nss, pam, ssh, autofs config_file_version = 2 domains = sunil.cc [domain/sunil.cc] id_provider = ad # Uncomment if service discovery is not working # ad_server = server.win.example.com default_shell = /bin/bash fallback_homedir = /home/%u [[email protected] db]#
Riavvia il servizio sssd.
[[email protected] db]# chkconfig sssd on [[email protected] db]# service sssd restart Stopping sssd: [ OK ] Starting sssd: [ OK ] [[email protected] db]#
Convalida utente.
[[email protected] db]# id sambauser uid=1570001105(sambauser) gid=1570000513(domain users) groups=1570000513(domain users),1570000512(domain admins),1570000572(denied rodc password replication group) [[email protected] db]#